
Don’t have a sandbox available for analysis of a phishing attempt? Here are ways to analyze and better understand email scams:
Analyze the Email Header
The header should be available via the email administration tool. In addition, the recipient can see the email header.
For example, in Gmail, after opening the email message, click on “…” on the top right side of the message and click on “Show Original” to see and copy the full header.
When looking at the email header, check for:
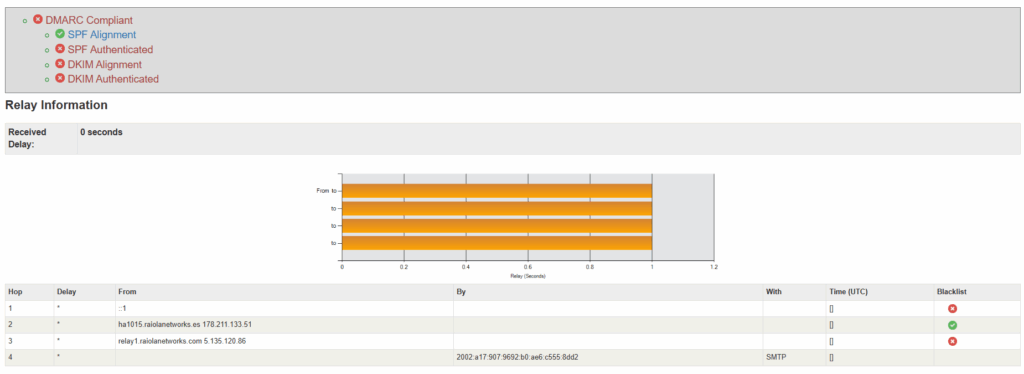
- SPF and DKIM authentication fails. Spoofed email messages will fail these if the domain has set them up.
- “Authenticated Sender” field in the header details, to see the actual sender email account.
- Sending IP address; this can be utilized during an investigation, via in your email administration client or firewall logs.
A free tool for grouping header data to be more readable: MXToolbox website (Analyze Header tab).
Analyze Links and Attachments
Any malicious links in the email message are included in the full header data. Instead of trying to copy the link from the original message, and risking accidentally clicking on the link, consider copying the link from the header.
Useful free tools for analyzing links and attachments:
- WhereGoes: (link analysis) shows the hops the link takes, to see the path and final destination.
- VirusTotal: (link or file analysis) evaluates malicious reports related to link or uploaded file per a number of malware databases.
- HybridAnalysis: (link or file analysis) captures sandbox screenshots of any pages where a link resolves as well as IP addresses. Analyzes links or uploaded files for malware and provides details on any processes that are launched by the link or file. This tool does not enter data if a link goes to a page requiring input. Also note: the analysis results are publicly available; do not upload attachments which may contain personal or other sensitive information.
Additional Assistance
If further analysis via a sandbox environment is needed, member organizations may send the full email header to MOREnet via security@more.net for sandbox analysis, also. MOREnet has a virtual environment which allows us to see and document the user experience of clicking on a link, entering data into a site, or opening an attachment.
