
Phishing campaigns using Portable Document Format (PDF) and Scalable Vendor Graphics (SVG) have greatly increased in the last year due to their flexibility and challenges for detection.
PDFs are the perfect transporter for malware as the file doesn’t look much different than a valid invoice or form. They can also contain embedded files and hidden objects. Hackers use these capabilities to create PDF files loaded with malware. Some red flags are:
- The file name may be generic or misleading or there is a double extension such as invoice.pdf.exe or document.pdf.scr. Toggle “show file extensions” to confirm it is an actual .pdf.
- The PDF is compressed in a ZIP or RAR to avoid detection by email filters.
SVGs are attractive to developers because they are scalable without loss of quality and their structure can be easily searched, indexed and compressed. These same features also make them very flexible and a dangerous attack vector. Because SVGs are code, JavaScript can be embedded to interact with the Document Object Model (DOM), executing scripts and other manipulative behavior. SVGs are frequently classified as low level image files such as PNG or JPEG. This results in filters and security software failing to do a deep inspection for the content beyond basic MIME-type checks, bypassing detection.
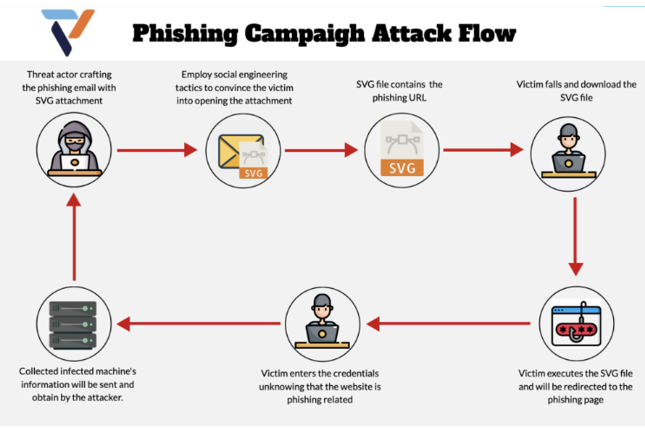
Below are indicators and preventative steps to reduce your risk:
- Message is not expected or is out of context.
- Subject line expresses urgency.
- Time to sign.
- You have a new voicemail.
- New vendor PO#.
- Payment confirmation.
- PDF apps and browsers should be up to date on security vulnerabilities.
- Confirm the device’s security software is being kept up to date.
- Use strong, unique passwords and MFA.
- Verify the sender and content. Call the sender to confirm.
- Scan the file with security software.
- Open in a sandbox environment.
- Implement cybersecurity training on a monthly or quarterly basis.
Combining vigilance with basic cybersecurity practices is key to mitigating your risk.
SVG Phishing Attacks – the New Trick in the Cybercriminals Playbook
