
Every school district is sitting on a goldmine of information. From attendance records and behavior reports to state assessment scores, the data is there—but it’s often trapped in silos, requiring hours of staff labor to organize, clean and analyze. By the time you have a clear picture of a student’s progress, the window for a timely intervention might have already closed.
MOREnet’s KIDS Ed-Fi is designed to change that. Built on the secure, scalable Ed-Fi standard in partnership with Education Analytics, KIDS Ed-Fi is more than just a storage solution—it’s a sustainable infrastructure that turns raw numbers into actionable insights in minutes.
One Solution, Two Perspectives
To ensure every stakeholder has the right tools, KIDS Ed-Fi delivers data through two specialized platforms: Rally and Podium.
Rally: Insight at the Classroom Level
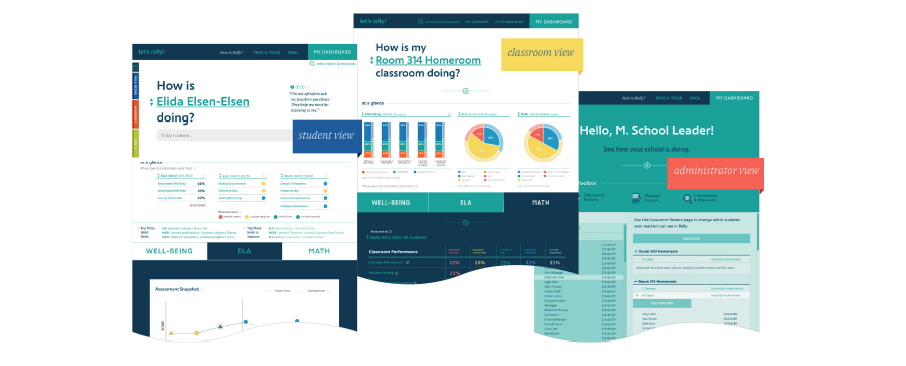
Rally is the daily companion for teachers and building administrators. It moves beyond “what happened” to “what’s next.” With intuitive dashboards, you can view student well-being surveys alongside academic passing rates.
The standout feature? Predictive analytics. Rally models past performance to allow teachers and school administrators to better understand all students’ paths to success.
Rally provides easier access to view individual student and aggregate level data by classroom, grade level and custom group, all in one place, including:
More Robust
Student Profiles
Custom grouping and intervention tracking to identify and monitor students who need supplemental support
Student
well-being data
Predictions of where students will score on end-of-year state assessments, modeled on past performance
Rally’s built in role-based security ensures that educators only see the data relevant to them. The platform integrates the following data into intuitive dashboards that provide insights at the student, classroom and grade level.
Podium: Strategy at the District Level
For education agency leaders, Podium provides a data visualization platform. Instead of getting lost in individual spreadsheets, leaders can visualize district-wide trends in chronic absenteeism, enrollment shifts and graduation tracks.
Podium empowers you to focus on systemic solutions. Whether you’re analyzing behavior data by student attributes or evaluating term-based grades to prevent dropouts, Podium ensures your decisions are backed by real-time evidence, not guesswork.
Designed to be actionable at multiple levels, Podium’s easily accessible set of dashboards include:
Insights on chronic absence so educators can identify which groups and students are at risk for targeted interventions
Behavior and discipline data analyzed by a range of student attributes
Term-based grades that can be analyzed to intervene with students who may be falling off-track for graduation
Assessment data and assessment history for currently enrolled students
Current enrollment data at a glance to evaluate trends and identify new or withdrawn students
A variety of profile dashboards that provide high-level summaries across data domains

KIDS Ed-Fi doesn’t just give you more data; it gives you your time back. By streamlining the data collection, school leaders can return to their true mission: planning and implementing the supports that help every student succeed.
Ready to learn more? Schedule a meeting with the KIDS team.
